Basis
nmap -sn [TARGET_NETWORK]/24Do not do port scan: scan for hosts (ARP, ICMP, TCP/UDP Ping).
nmap -sV -sC [TARGET_IP]Ports services + Default script.
Host dicovering Process (-sn)
- Privileged user scans targets in local network: ARP requests.
- Privileged user scans targets outside local network: ICMP echo requests, TCP ACK to port 80, TCP SYN to port 443, and ICMP timestamp request.
- Unprivileged user scans targets outside local network: SYN to ports 80 and 443.
Flags
-OOS detection.
-sVService detection (Force Nmap to proceed with the TCP 3-way handshake).
-oN myOutputFileNormal Output.
-vvVerbose.
-nDo not resolve DNS.
-PnDo not ping to determine if host is up.
-rScan the ports in consecutive order instead of random order.
Ports
-p 80Scan port 80.
-p 80,443Scan ports 80 and 443.
-p 80-443Scan ports 80 to 443.
-p-Scan all ports.
Timing
-T0Paranoid (5 minutes between sending each probe/ Avoid IDS Dectection).
-T1Sneaky (Avoid IDS Dectection).
-T2Polite.
-T3Normal (Default).
-T4Aggressive.
-T5Insane (Can affect scan accuracy)
Scans Types
-sTTCP connect scan. Default running with non privileged users.
-sSSYN scan (Half TCP / “Sneaky”). Default running with privileged users.
-sUUDP port scan.
Firewall Bypass and Evasion
-sNNull scan (do not set any TCP flag). No response is either port open or filtered.
-sFFIN scan (FIN flag). No response is either port open or filtered.
-sXXmas scan (FIN, PSH, and URG flags simultaneously). No response is either port open or filtered.
-AUsed to discover firewall rules. Return unfiltered ports (dosn't mean they're up).
-D [TARGET_IP]RND,MESend same request with decoy IP addresses (RND is Random IP and ME is my IP).
-f and -ffSend fragmented packets (divided into 8 and 16 bytes).
Scripts
/usr/share/nmap/scripts
-sCDefault script scanning.
-AAgressive Scan (-O + -sV + -sC + --traceroute).
--script vulnRun a script.
--script http-put --script-args http-put.url='https://security.kaldei.xyz/dav/shell.php',http-put.file='./shell.php' Script with arguments
SMB Scan
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse [TARGET_IP]Search for SMB Shares.
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount [TARGET_IP]Enumerate rpcbind.
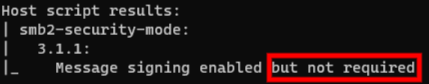
nmap --script=smb2-security-mode.nse -p445 [TARGET_IP]Scan for disabled SMB Signing.
Weak Cipher Scan
nmap --script=ssl-enum-ciphers -p 443 [TARGET_IP]Check for weak cipher. Under B score, it’s a bad cipher.
